Revolutionized is reader-supported. When you buy through links on our site, we may earn an affiliate commision. Learn more here.
Stolen passwords and credentials are among the most common methods hackers use to steal information. To prevent an influx of even more breaches, use these strategies to protect your accounts. Even one of these tips will reinforce your data security, with every subsequent action making defenses even stronger.
Let’s start with simple techniques that take minimal time and cybersecurity literacy to implement.
Many websites have required users to change their default passwords to comply with the most recent agency recommendations. However, if a platform does not have these rules in place, make passwords long and complicated, incorporating these elements:
It could feel tempting to use a birthday or a loved one’s name as part of the password. However, this information is easily accessible to hackers from publicly viewable platforms, such as social media. This makes it straightforward for a threat actor to gain access to an account and steal sensitive data. Here are a few other pieces of information to avoid in your passwords:
This type of information, albeit in a more specific context, is often used in authenticating questions anyway. Save these responses for those fields to lower the risk of stolen passwords.
While every website, application and shop demands a unique account, you should never reuse a password for anything. Remembering potentially hundreds of specific passwords may feel impossible, but there are numerous organization methods to store everything in a safe place.
This is time-consuming to set up, but simple to manage once you put in the effort. It is worth it because you have reduced the power of a single password to jeopardize countless digital assets.
Remembering strings of random numbers, letters and characters is a lofty expectation. Instead, cybersecurity analysts recommend using a password that contains a phrase. The best way to structure the password is to write a sentence and transform it into a usable password using the industry’s recommendations, such as incorporating special symbols.
Try writing a personal story that only you would know, so it is even harder to guess. This makes the password more straightforward to remember, but it is equally complicated.
Example sentence: I made a cherry cake for mom’s birthday.
Example passphrase: Bakedcherry!Cake4Mom
If you have tried all the aforementioned methods, you can consider incorporating additional, more thorough measures.
Many companies have created managers to organize and encrypt all your different passwords, which are locked behind several authentication measures, such as a master password or biometrics. Many of these services include additional features, such as security scans, breach notifications and password generators. If you don’t want to pay for one, many browsers have them embedded and usable for free.
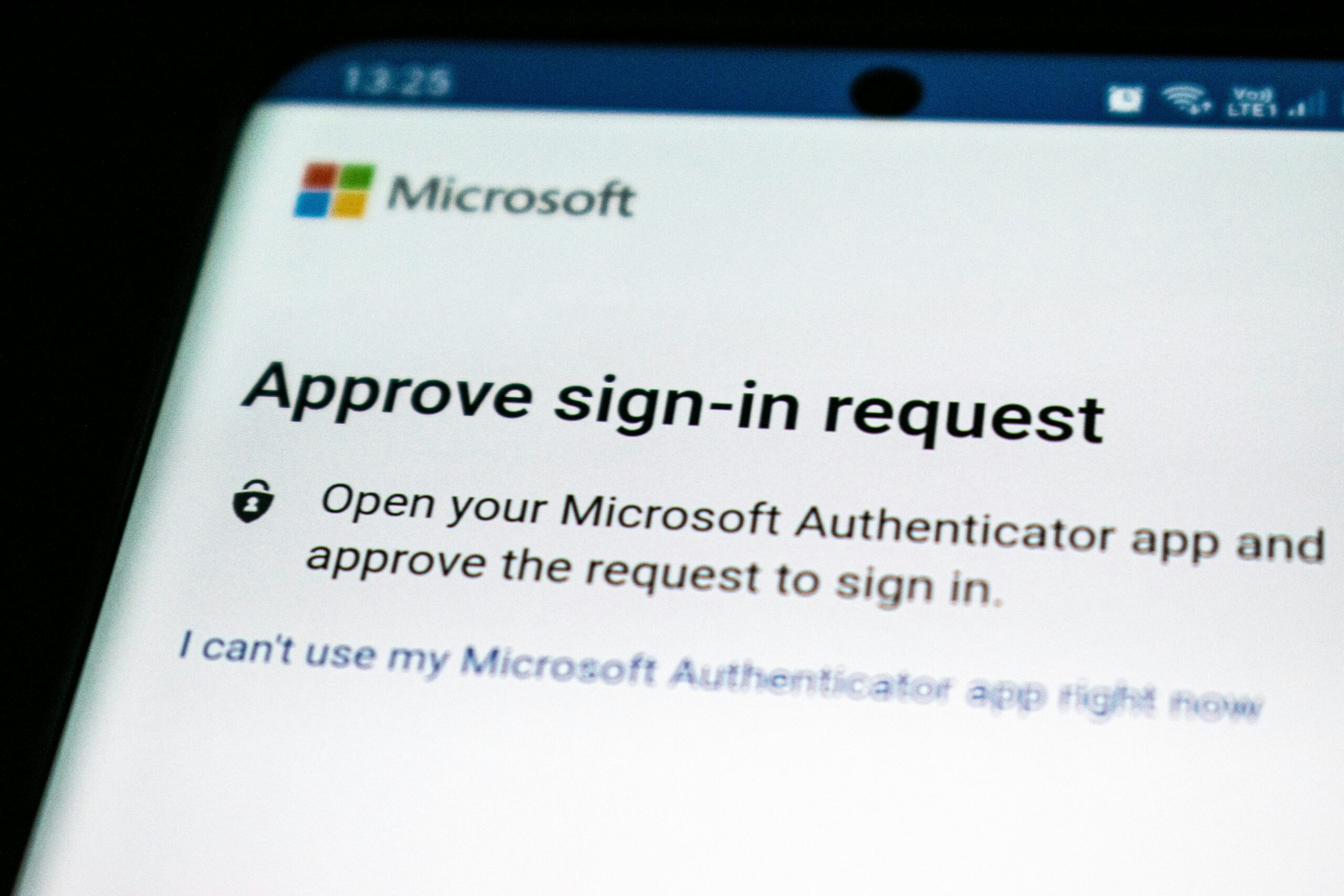
You can enable multifactor authentication on almost any platform. It requires another login method in addition to a password. They can include:
You can sign up for services that regularly scan your email to see if it has been part of a data breach. Many password managers also do this. If you receive a notification that your credentials have been compromised, change them immediately.
Phishing scams have expanded in scope, with numerous variants now existing. Even artificial intelligence-based phishing scams are becoming increasingly common, requiring everyone to be skeptical of everything that lands in their inbox. They are one of the most common breach types in history, so always be cautious when opening emails, links and attachments from unknown sources.
Every individual can continually enhance their security posture. If you are still concerned with the depth of your protective strategies, use these expert-recommended tips to become one of the smartest password protectors.
You could also eliminate the need for passwords entirely by using passwordless strategies. Many login methods you find in MFA are usable as a first option. You can also use hardware security keys for even higher security.
Keep cybersecurity news in your feeds to stay informed. Cybercriminals are creative, continually developing new tactics to manipulate credentials and the individuals who own them. Stay ahead of the curve by learning about new threat types and the methods hackers use to steal information.
Your most important accounts deserve their own email address to keep information separated from the majority of your online presence. Online profiles that manage your health, career or finances can be delegated to another place to make it even more challenging for hackers to sneak their way in. If you’re concerned about profiles like investment accounts or health data, create unique emails for each one, but try not to create so many that you can’t juggle them all.
NIST is one of the leading organizations for cybersecurity frameworks. Its experts create models for businesses and individuals, and many of its tips are applicable to home use.
The password guidelines have undergone significant changes over the years, including the removal of recommendations for frequent password changes. Research slowly revealed that this actually made accounts more susceptible to breaches, so they altered their guidelines. This illustrates the sector’s development and the opportunities for adaptation.
You should never have to worry about your information being stolen, but it could happen if you don’t do something to safeguard your credentials and data. Make it a goal to implement at least one of these measures today, and a few others in the coming weeks. The more you use, the more likely you are to resist the attacks of any cybercriminal.
Revolutionized is reader-supported. When you buy through links on our site, we may earn an affiliate commision. Learn more here.

This site uses Akismet to reduce spam. Learn how your comment data is processed.